When it comes to choosing a cybersecurity framework, two heavyweights often come up: SOC 2 and NIST. Both frameworks aim to boost your organization’s security game, but they cater to different needs. This guide will break down these two frameworks, explain their key components, and highlight the major differences to help you figure out which one is the best fit for your company.
Understanding SOC 2
Let’s start with SOC 2 certification. It stands for Service Organization Control 2, and it’s a SOC framework designed by the American Institute of Certified Public Accountants (AICPA). SOC 2 is all about protecting data and ensuring that service organizations, like Software as a Service (SaaS) providers, handle customer information securely.
SOC 2 is particularly important for businesses that deal with sensitive customer data, such as SaaS companies, cloud computing providers, and other tech-based service organizations.
Key Components of SOC 2
At the core of SOC 2 are the five trust service criteria (TSCs). These criteria form the foundation for SOC 2 compliance:
- Security: Making sure that systems are protected from unauthorized access, whether that be hacking or internal misuse.
- Availability: Ensuring that systems are available for use when needed, based on agreements between the service provider and customers.
- Processing Integrity: Making sure that data processing is accurate, complete, and authorized.
- Confidentiality: Ensuring that any confidential information is properly protected.
- Privacy: Addressing the system’s collection, use, retention, and disposal of personal information according to the company’s privacy policy.
SOC 2 Certification Reports
SOC 2 audits come with two types of reports: Type I and Type II.
- Type I: Describes the systems and processes in place at a certain point in time and whether they meet the trust principles.
- Type II: Shows how effective those systems and processes are over a defined period.
Understanding NIST
NIST, short for the National Institute of Standards and Technology, operates under the U.S. Department of Commerce. NIST frameworks, like NIST CSF compliance, provide organizations with guidelines to enhance their cybersecurity resilience. It’s especially popular for its flexibility, allowing businesses to tailor it to their specific needs.
Key Components of NIST
NIST offers a bunch of frameworks, but let’s focus on the ones most relevant for cybersecurity:
- NIST Cybersecurity Framework (CSF): This one is all about helping organizations manage and reduce their cybersecurity risks. It focuses on five main areas: Identify, Protect, Detect, Respond, and Recover.
- NIST 800-53: This is a catalog of security and privacy controls, mostly aimed at federal information systems but widely used beyond that. It’s great for organizations looking for a more structured and prescriptive approach to cybersecurity.
- NIST 800-171: Tailored for non-federal entities that handle Controlled Unclassified Information (CUI), this framework helps protect sensitive federal data.
Key Differences Between SOC 2 and NIST
Now that we’ve got the basics of both frameworks down, let’s dive into the key differences between SOC 2 and NIST.
Scope and Applicability
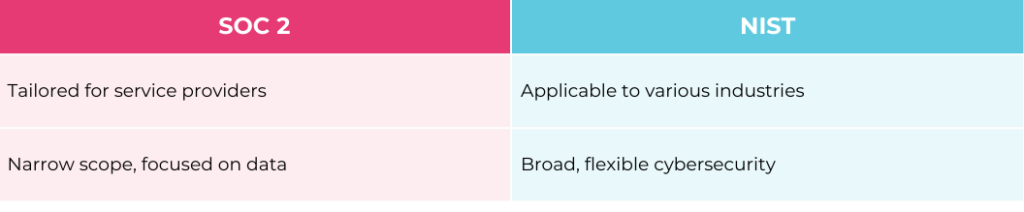
- SOC 2 is designed for service organizations like SaaS providers, with a heavy focus on the protection of customer data. Its scope is narrower, targeting specific industries and use cases.
- NIST is a lot broader in scope and can be applied to a wide range of organizations, from tech startups to government agencies. It’s ideal for organizations looking for a flexible and customizable cybersecurity framework that covers a range of security needs.
Focus
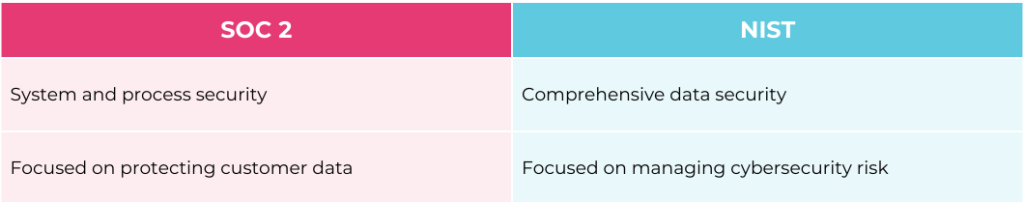
- SOC 2 zeroes in on the systems and processes in place to safeguard customer data. It’s all about making sure the service organization is managing and protecting data securely.
- NIST takes a more data-centric approach, offering guidelines and best practices to improve cybersecurity resilience overall. NIST focuses on risk management across the entire business, not just customer data.
Certification and Audits
- SOC 2 certification is pretty formal—organizations need to go through a third-party audit, and there are official Type I and Type II reports that document compliance. SOC 2 audits are common for companies needing to show compliance to their customers or business partners.
- NIST, on the other hand, doesn’t have an official certification process. It’s more of a guideline for organizations to follow, without the requirement for independent audits.
Implementation
- SOC 2 requires organizations to implement and maintain controls that protect data according to the five trust principles. It’s not super prescriptive, but you’ll need to work with auditors and invest in resources to ensure compliance.
- NIST frameworks offer more flexibility, letting organizations implement them according to their own specific needs. However, due to their comprehensive nature, you’ll need a good understanding of your organization’s structure and the different control families.

Choosing Between SOC 2 and NIST
So, which framework is better for your organization? That depends on several factors, including your business model, industry requirements, and risk tolerance.
Business Operations
If you’re a SaaS provider or a service-based business, SOC 2 might be a better fit. SOC 2 is built for companies that need to ensure the security and availability of customer data, making it ideal for businesses in tech, finance, and healthcare.
On the other hand, if your business operates in various sectors and needs a more versatile approach to cybersecurity, NIST could be the right call. NIST frameworks are designed to adapt to different industries and business models, offering a broad set of tools to manage cybersecurity risks.
Industry Requirements
Many businesses choose SOC 2 because it’s often a requirement by customers, business partners, or even regulators, especially in industries like finance and healthcare where data security is paramount.
NIST, however, is widely used by government agencies and contractors. If you need to comply with federal regulations or work with government bodies, following a NIST CSF compliance strategy is a smart move.

Risk Tolerance
NIST frameworks provide a risk-based approach, helping you identify and manage risks across your organization. If you’re focused on structured risk management, NIST might give you a more robust approach for managing cybersecurity threats.
SOC 2, on the other hand, is all about the security, availability, processing integrity, confidentiality, and privacy of customer data. This makes it slightly more resource-intensive but ensures you’re constantly meeting the trust principles.
Resource Availability
If you’re tight on resources but still need a robust cybersecurity framework, NIST might be a good option. It’s flexible and can be scaled according to your organization’s needs. However, you’ll still need to have a strong understanding of your business’s structure and risks.
SOC 2, while more prescriptive, involves third-party audits and ongoing maintenance of security controls. It’s more suited for companies that can invest in compliance teams and auditors.
ISO 27001: Another Framework to Consider
While SOC 2 and NIST are popular, ISO 27001 is another widely recognized framework that focuses on information security management. It provides a systematic approach to managing sensitive company information, making it a key contender for businesses aiming to secure their data and processes. For companies exploring SOC 2 alternatives, ISO 27001 offers a robust solution that can be integrated alongside other frameworks to ensure a well-rounded security posture.
Costs and Resources for SOC 2 and NIST Implementation
Implementing SOC 2 and NIST can require a significant investment of time, money, and resources. However, the benefits of improved security and compliance often outweigh the costs.
- SOC 2 Costs: SOC 2 certification can be expensive, particularly for smaller organizations. The costs of the audit, the time spent preparing for the audit, and any necessary upgrades to security infrastructure can add up quickly. Additionally, SOC 2 requires ongoing monitoring, which means continuous investment in security measures and audits.
- NIST Costs: NIST, on the other hand, is a voluntary framework that does not involve external audits. As such, the direct costs of NIST implementation are typically lower than those for SOC 2. However, NIST can still be resource-intensive, as it requires organizations to develop and maintain a comprehensive cybersecurity program, including regular risk assessments, staff training, and the implementation of technical controls.
- Cost Savings Through Automation: One way to reduce the costs of SOC 2 and NIST implementation is to leverage automation. Solutions like Scytale’s compliance automation tools can streamline the process of mapping controls, tracking compliance progress, and generating reports. Automation not only saves time but also reduces the risk of human error, making it easier to maintain compliance with both SOC 2 and NIST frameworks.
GET SOC 2 COMPLIANT 90% FASTER
The Role of Third-Party Auditors and Consultants
For organizations pursuing SOC 2 certification, working with a third-party auditor is essential. Auditors play a critical role in assessing whether an organization’s systems and controls meet the trust service criteria outlined by SOC 2.
Choosing the right auditor is an important step in the SOC 2 process. Look for auditors who specialize in SOC 2 assessments and who have experience working with organizations similar to yours. A knowledgeable auditor can provide valuable insights into the SOC 2 process and help identify areas for improvement.
Similarly, for organizations implementing NIST frameworks, working with a consultant can be beneficial. A cybersecurity consultant with expertise in NIST frameworks can assist in developing a tailored risk management plan and ensure that all necessary controls are in place
SOC 2 and NIST: Complementary Approaches
While SOC 2 and NIST are distinct in their scope and purpose, it’s worth noting that these frameworks are not mutually exclusive. In fact, many organizations find value in leveraging both to create a more comprehensive security posture.
For example, a company may adopt NIST frameworks, such as NIST CSF, for its broad and flexible approach to cybersecurity risk management, while also seeking SOC 2 certification to meet customer expectations and industry requirements regarding data protection. By combining the strengths of both frameworks, organizations can address a wider array of security challenges.
Integrating SOC 2 and NIST
Organizations that wish to use both SOC 2 and NIST frameworks can take a strategic approach to integrate these standards effectively. Here’s how this can be done:
- Identify common controls: Start by identifying the controls that overlap between SOC 2 and NIST. For instance, both frameworks require robust access controls, incident response plans, and encryption measures. By mapping out the commonalities, organizations can streamline the implementation process and avoid duplication of efforts.
- Tailor the frameworks to business needs: While SOC 2 focuses on trust service criteria and NIST provides a broader set of guidelines, organizations can tailor each framework to their specific needs. For example, if your organization handles sensitive customer data, SOC 2’s privacy criteria may be more applicable, while NIST’s risk management guidelines can provide a foundation for addressing broader security concerns.
- Use a layered approach: SOC 2 and NIST can be used together to create layers of protection. SOC 2 can ensure that customer data is handled securely and meets compliance requirements, while NIST’s guidelines can offer a broader framework for identifying and mitigating cybersecurity risks across the entire organization.
- Continuous monitoring: Both SOC 2 and NIST emphasize the importance of ongoing monitoring and improvement. SOC 2 Type II reports focus on operational effectiveness over time, while NIST encourages continuous risk assessments and updates to security controls. By implementing continuous monitoring strategies, organizations can ensure that their cybersecurity posture remains strong and adaptable.
Ongoing Compliance and Future Trends
Once SOC 2 or NIST frameworks are implemented, it’s important to remember that compliance is an ongoing process. Cybersecurity threats are constantly evolving, and organizations need to stay vigilant to maintain compliance and protect their data.
- SOC 2 recertification: SOC 2 certification is not a one-time event. Organizations must undergo regular audits (usually annually) to maintain their certification. Additionally, SOC 2 Type II reports require evidence of operational effectiveness over time, meaning organizations must continually monitor and document their security practices.
- NIST updates: NIST frameworks are regularly updated to reflect changes in the cybersecurity landscape. Organizations that adopt NIST should stay informed about new guidelines and adjust their security measures accordingly. For example, updates to NIST 800-53 or NIST 800-171 may introduce new controls or requirements that organizations need to implement.
- Emerging technologies: As technology continues to advance, both SOC 2 and NIST will need to adapt to address new security challenges. For instance, the rise of artificial intelligence (AI), machine learning (ML), and the Internet of Things (IoT) introduces new risks that organizations must manage. As these technologies become more prevalent, expect to see new controls and guidelines that address their specific security concerns.
Next Steps for Organizations
If you’re ready to start your journey toward SOC 2 or NIST compliance, here are a few practical steps to get you started:
- Conduct a gap analysis: Begin by conducting a thorough gap analysis to identify where your organization stands in relation to the requirements of SOC 2 or NIST. This will help you understand what controls and processes need to be implemented or improved.
- Develop a compliance plan: Create a detailed compliance plan that outlines the steps your organization will take to meet the requirements of SOC 2 or NIST. This plan should include timelines, resource allocation, and responsibilities.
- Engage with experts: Consider working with compliance experts, auditors, or consultants who can provide guidance and support throughout the implementation process. Their expertise can help streamline the process and ensure that all necessary controls are in place.
- Leverage automation: Utilize automation tools, like Scytale’s compliance platform, to simplify the compliance process. Automation can help you track progress, monitor controls, and generate the necessary documentation for audits.
- Monitor and adjust: Compliance is an ongoing process, so it’s important to continuously monitor your security controls and make adjustments as needed. Regular reviews and updates will ensure that your organization stays compliant and prepared for any changes in the cybersecurity landscape.
By following these steps and leveraging the strengths of SOC 2 and NIST, your organization can build a robust cybersecurity program that not only meets compliance requirements but also protects sensitive data and fosters trust with customers and stakeholders.
Conclusion
When it comes to beefing up your cybersecurity, both SOC 2 and NIST bring something special to the table. But they’re designed with different goals in mind.
If you’re running a service-based business, SOC 2 is your go-to. It’s perfect for keeping customer data safe and checking off those industry-specific boxes. Plus, the external audits give you some serious street cred when it comes to security.
On the other hand, NIST is like a Swiss Army knife for cybersecurity—it’s super flexible and fits a variety of industries. Whether you need to tackle a specific risk or overhaul your entire security setup, NIST’s got your back with a risk-based, customizable approach.
The bottom line? Knowing the difference between these two frameworks helps you choose what makes the most sense for your business. Whether you stick with SOC 2, dive into NIST, or go for both, you’ll be setting yourself up for stronger security and gaining some major trust points with your customers. And who doesn’t want that?