Learn the essentials of South Africa's POPIA, its impact on data protection, and how it compares to global privacy laws.
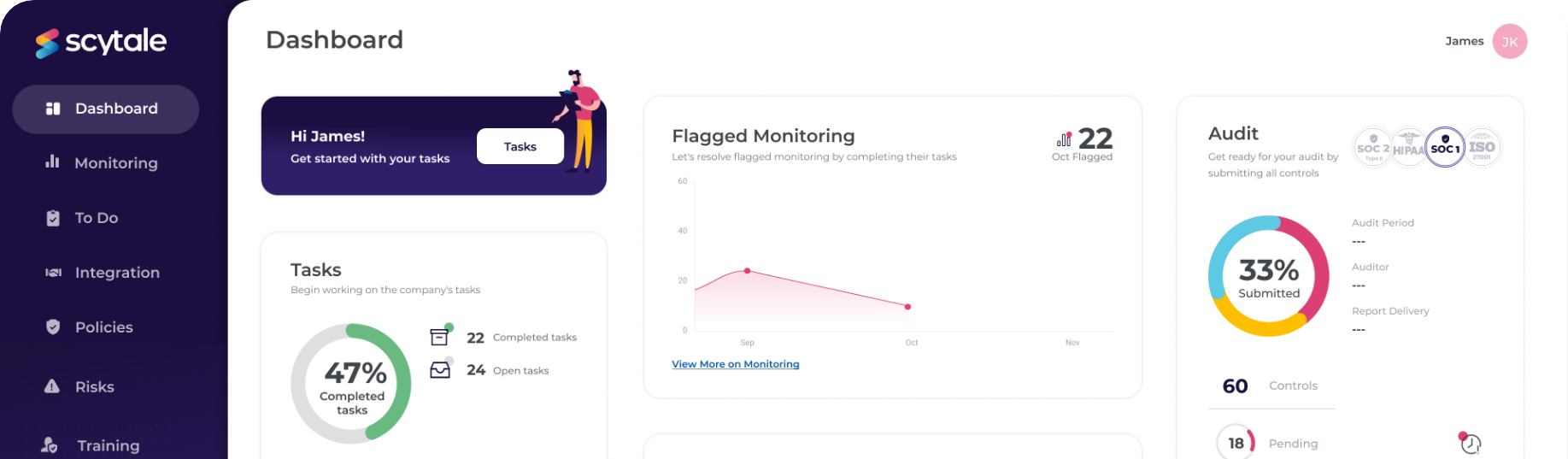






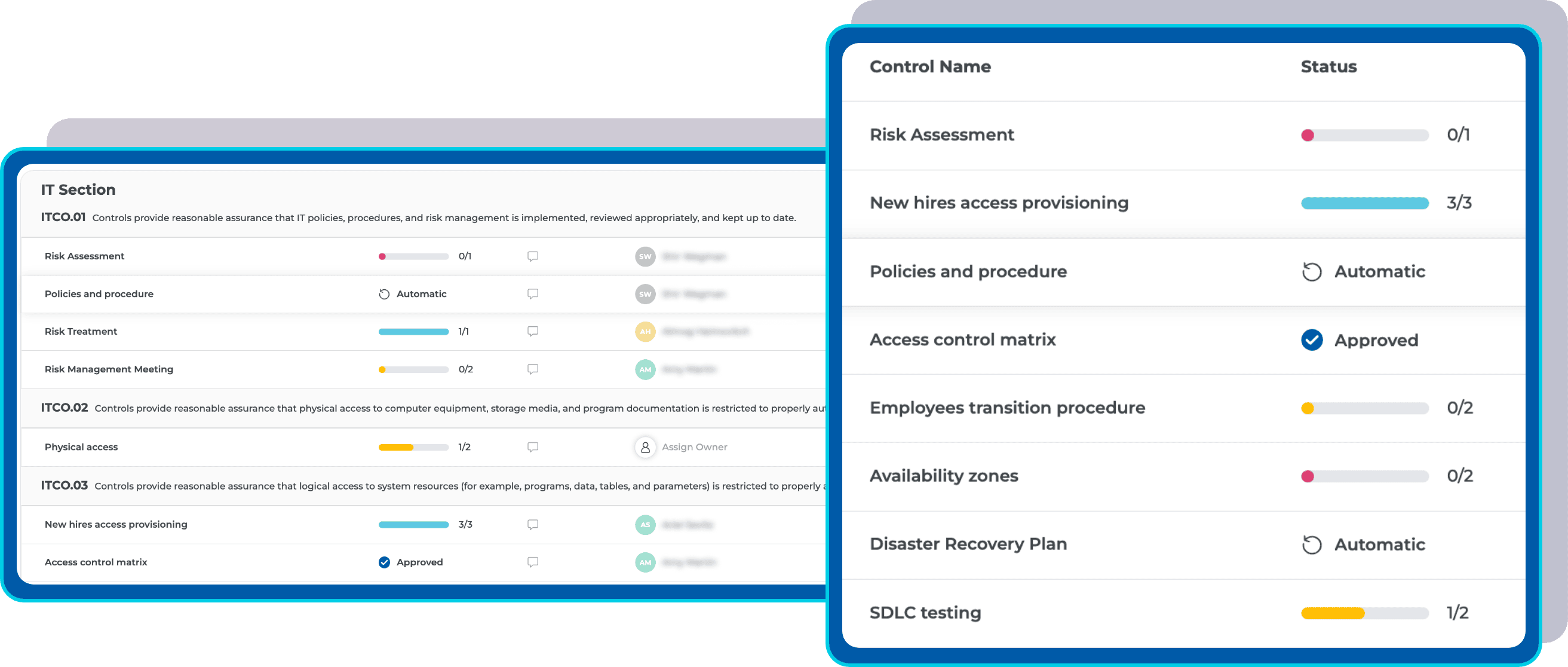
Receive a customized controls list and leverage IT general controls mapped from your SOC 2 audit.

If your head is spinning from all the SOC 1 requirements, then you’ve come to the right place! Our experts guide you each step of the way, ensuring you’re fully prepared to ace your audit.

Our super experienced compliance experts customize your business process controls and define the scope of your audit for you. Feeling less stressed already?

We know about the thousands of emails and zoom meetings that are involved with your auditor. That’s why we manage all communication and requests for you with your chosen auditor.


Build trust in your IT and business process controls relevant to financial reporting with automated SOC 1 compliance.

Automate your audit-readiness process and boost customer trust by complying with the AICPA's Trust Services Criteria.

Ensure you're storing, managing and transferring protected health information (PHI) securely and automate your HIPAA compliance.

Make sure you're securing payments and cardholder data correctly with smooth-sailing PCI DSS compliance.

Increase trust in your compliance measures to protect sensitive defense data with streamlined technology.

Effortlessly meet the security and privacy controls for U.S. federal information systems with compliance automation.
“The system is easy to use and integrations save plenty time. But the best feature is the team. Scytale was the secret sauce to get us there in record-breaking time.”
Yahel G.
Head of Operations, Computer Software

“Working with Scytale was an accelerator for our company, helping us to stay focused on SOC 2 requests and pass the examination much faster than expected.”
Paz D.
CTO, Information Technology and Services

“Not only does their platform make it really easy to divide tasks between the team, the service they offer makes you feel like you have your own compliance team.”
Bradley A.
Co-Founder, Insurance

“Before Scytale, we ran around like headless chickens to gather evidence all over the place, digging deep into archives. With Scytale, evidence auto-collects itself.”
Maayan N.
Manager of Operations, Computer Software


Learn the essentials of South Africa's POPIA, its impact on data protection, and how it compares to global privacy laws.
Secure your data with PCI penetration testing—essential for protecting credit card information, staying compliant, and avoiding breaches.
Streamline compliance with Scytale's new Jira integration! Sync tasks seamlessly, enjoy two-way status updates, and simplify ...
This blog dives into the top 10 compliance automation tools for 2024 to streamline your regulatory processes with ease.
Hear from our compliance expert, Ronan Grobler, as he gives a quick rundown on ISO 42001 and its role in the age of AI.
Check out Scytale's CEO, Meiran Galis, on the The Matias Experiment podcast as he talks about his journey.
How creating a comprehensive SOC 2 scope can benefit your business, and how to get there.
Scytale named G2's summer 2024 Leader in governance, risk, & compliance, Momentum Leader, & High Performer in cloud and security compliance!
Scytale's DPO & Compliance Success Manager, Tracy Boyes, addresses whether vendors need to be HIPAA compliant if their customers are.
Scytale's DPO & Compliance Success Manager, Tracy Boyes, breaks down how Scytale can assist you in achieving compliance with POPIA.
Scytale's DPO & Compliance Success Manager, Tracy Boyes, talks about the difference between HIPAA and POPIA.
Discover how the NIS2 Directive enhances EU cybersecurity and protects digital assets. Learn why compliance is crucial for your business.
A SOC 2 readiness assessment is a way of examining your systems to make sure it’s compliant with security controls of the SOC 2 standard.
Scytale joins the AWS ISV Accelerate Program to enhance its cloud compliance solutions with better performance and reliability.
As you prepare your business strategy for the second half of 2024, regulatory compliance automation should be a top priority.



