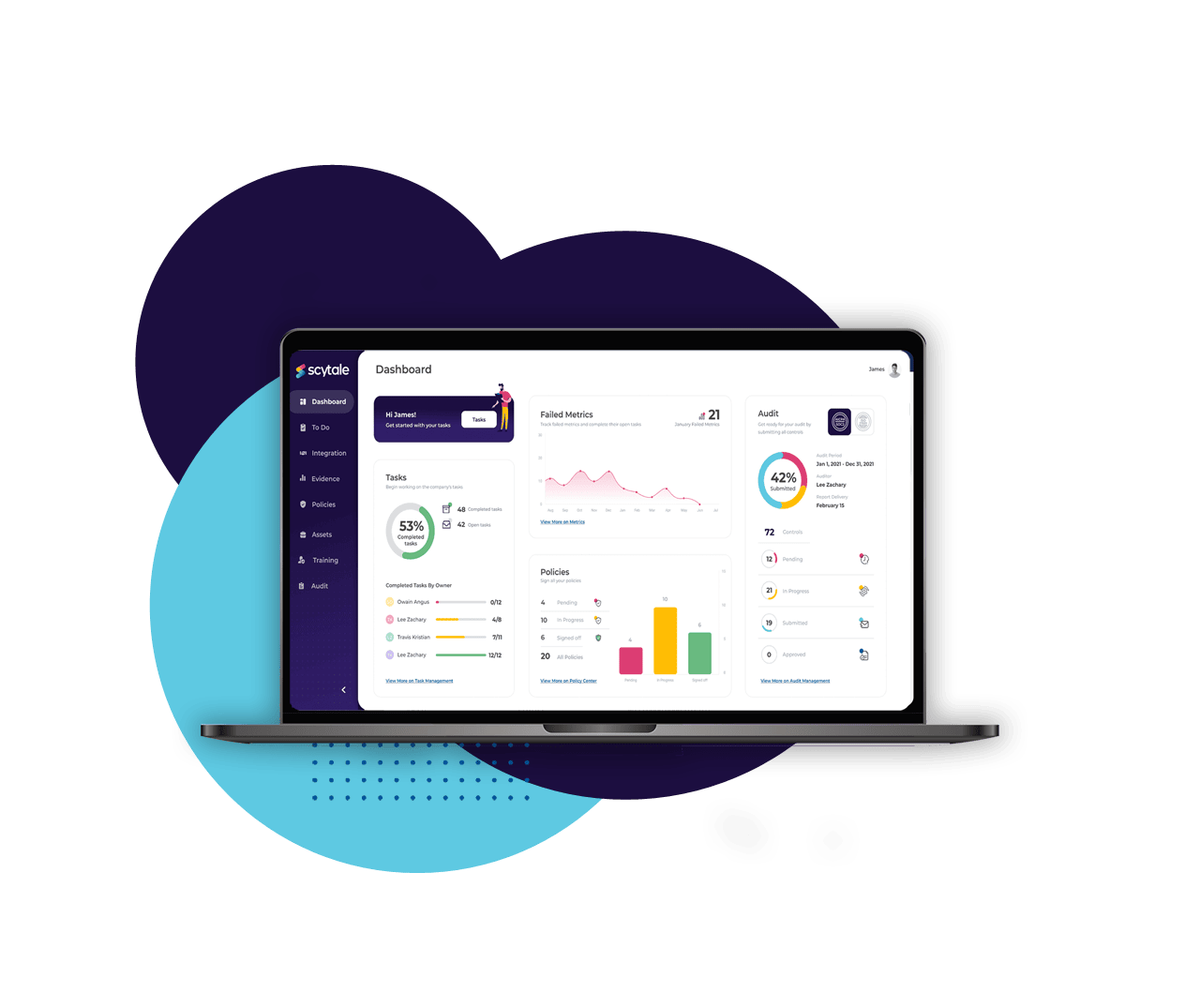
Compliance Automation Technology
Power-up your automated evidence collection, continuous control monitoring and smart audit management.

An Expert Team That
Does It All For You
Don’t have an in-house expert? Get a Dedicated Compliance Expert from start to finish of your compliance process.